In recent years, Intel processors have revealed many vulnerabilities starting with Meltdown and Specter which are associated with speculative execution of instructions based on branch prediction. Although many vulnerabilities are already covered by software patches security researchers are constantly finding new ones.
Another vulnerability was called CrossTalk (Intel uses the name SRBDS – Special Register Buffer Data Sampling, and in the vulnerability catalogue it carries the identifier CVE-2020-0543). Unlike previously discovered vulnerabilities, the new one allows a malicious program to steal data from programs executed by other kernels using a common buffer. However, software updates released to close Meltdown and Specter are helpless. Note that the attack is successful in processors without HyperThreading.
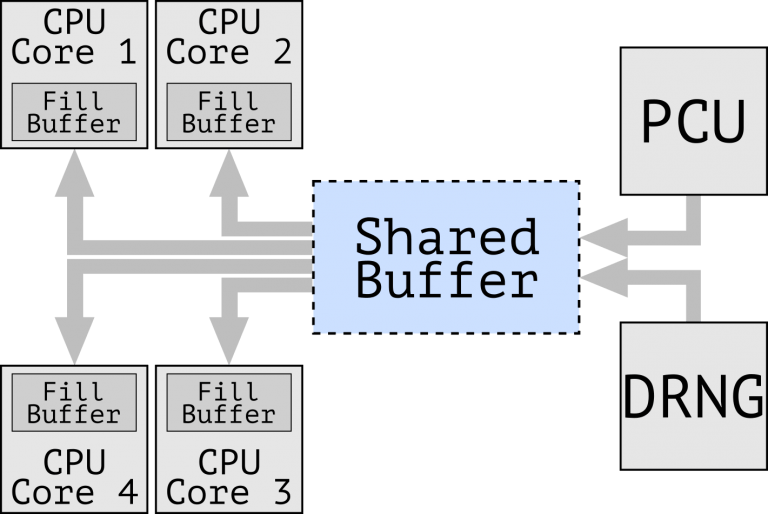
According to the source, CrossTalk carries a rather big danger for users of systems used together. For example: cloud computing.
Also Read: AMD Ryzen 3000XT Processors were Listed Online by French Retailer
Intel not only knows about the problem but also released a patch (in fact, after that it became possible to publish information about CrossTalk). Vulnerability is in the server, desktop, mobile and embedded processors. The full list is huge and is published on the Intel website.





